← meaning trust Meaningful quotes what is the meaning of trust in a business What is business-to-business trust? →
If you are searching about What is Cloud Computing? Definition, Meaning, and Examples you've came to the right web. We have 35 Pics about What is Cloud Computing? Definition, Meaning, and Examples like Welcome To Trusted Computing Group | Trusted Computing Group, cyber attacks trusted computing software – TechCodex and also Overview of Ahoi Attacks | Ahoi Attacks. Read more:
What Is Cloud Computing? Definition, Meaning, And Examples
 www.enkash.com
www.enkash.com
Welcome To Trusted Computing Group | Trusted Computing Group
 trustedcomputinggroup.org
trustedcomputinggroup.org
trusted computing group tcg logo toggle navigation
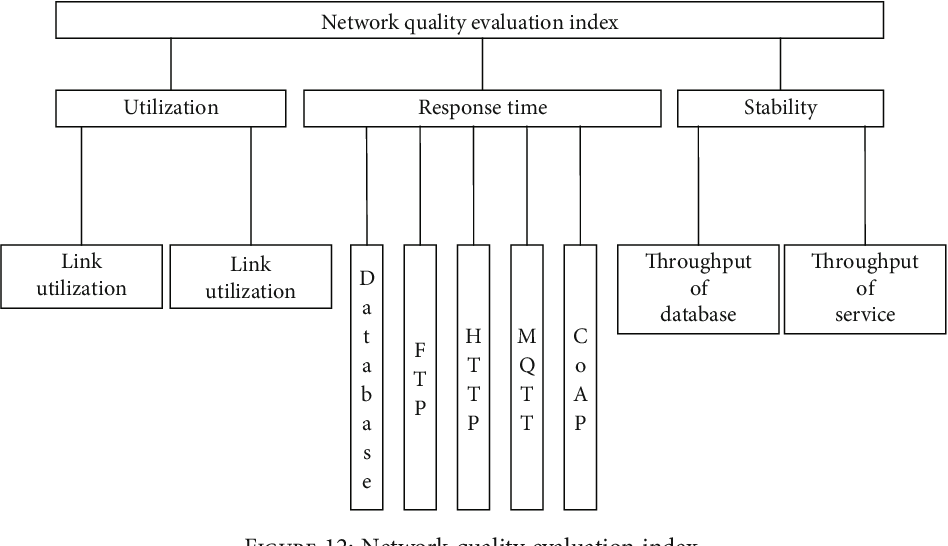
2025 4th International Conference On Cybersecurity, Artificial
 www.csaide.net
www.csaide.net
Figure 1 From Power IoT System Architecture Integrating Trusted
 www.semanticscholar.org
www.semanticscholar.org
Thread By @avalancheavax On Thread Reader App – Thread Reader App
 threadreaderapp.com
threadreaderapp.com
(PDF) A Federated Learning Multi-Task Scheduling Mechanism Based On
 www.researchgate.net
www.researchgate.net
SOLUTION: Cyber Threat Intelligence Security Information And Event
 www.studypool.com
www.studypool.com
The Trusted Platform Module Specifications - DocsLib
 docslib.org
docslib.org
Introduction To TPM (Trusted Computing Module) - Prog.World
 prog.world
prog.world
TPM 2.0: The New Standard For Secure Firmware - Help Net Security
 www.helpnetsecurity.com
www.helpnetsecurity.com
Trusted Computing Base Patented Technology Retrieval Search Results
 eureka.patsnap.com
eureka.patsnap.com
Cyber Attacks Trusted Computing Software – TechCodex
 techcodex.com
techcodex.com
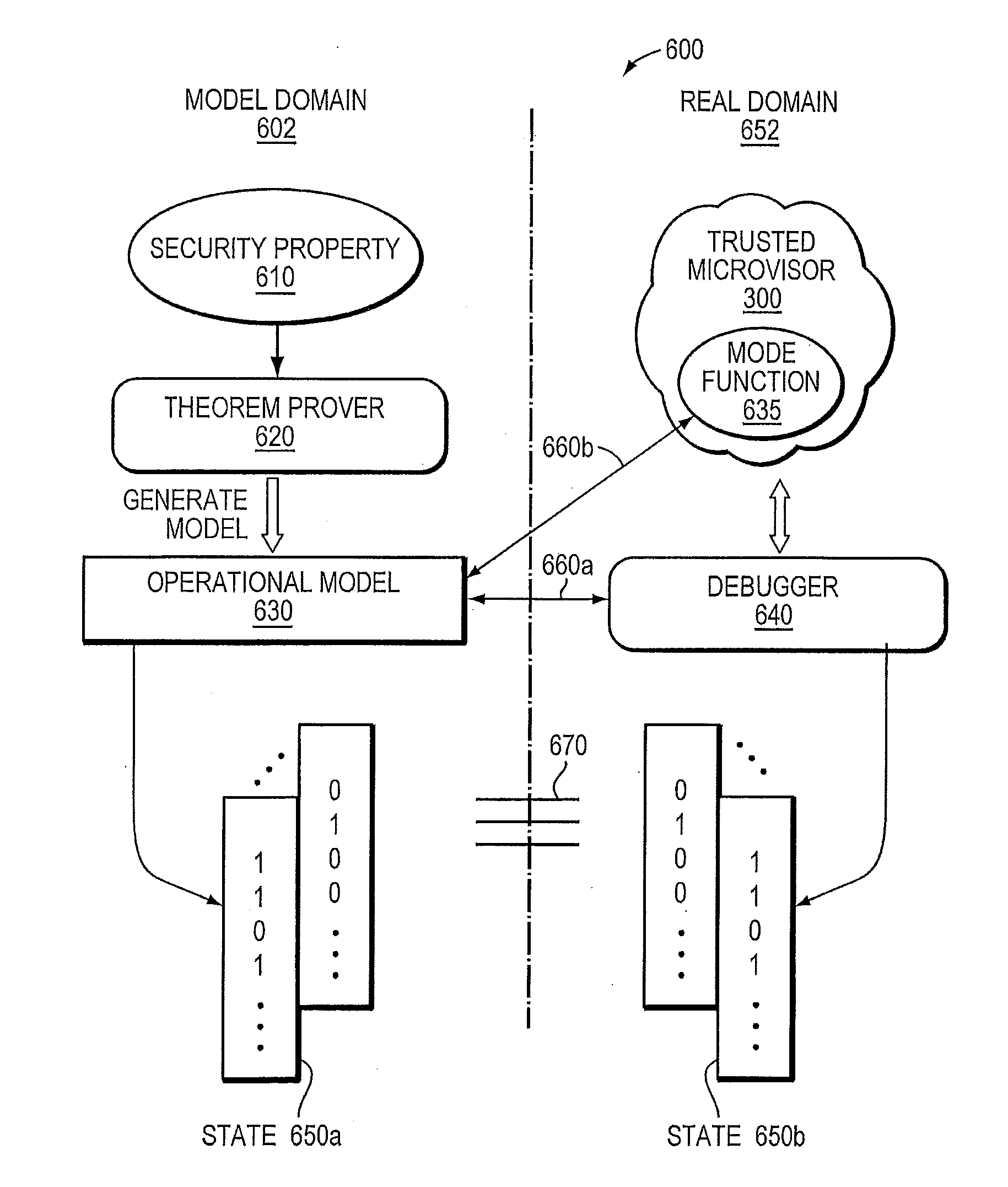
Figure 1 From Trusted Networks: Design Of An RFID Trusted Reader (D4.4.
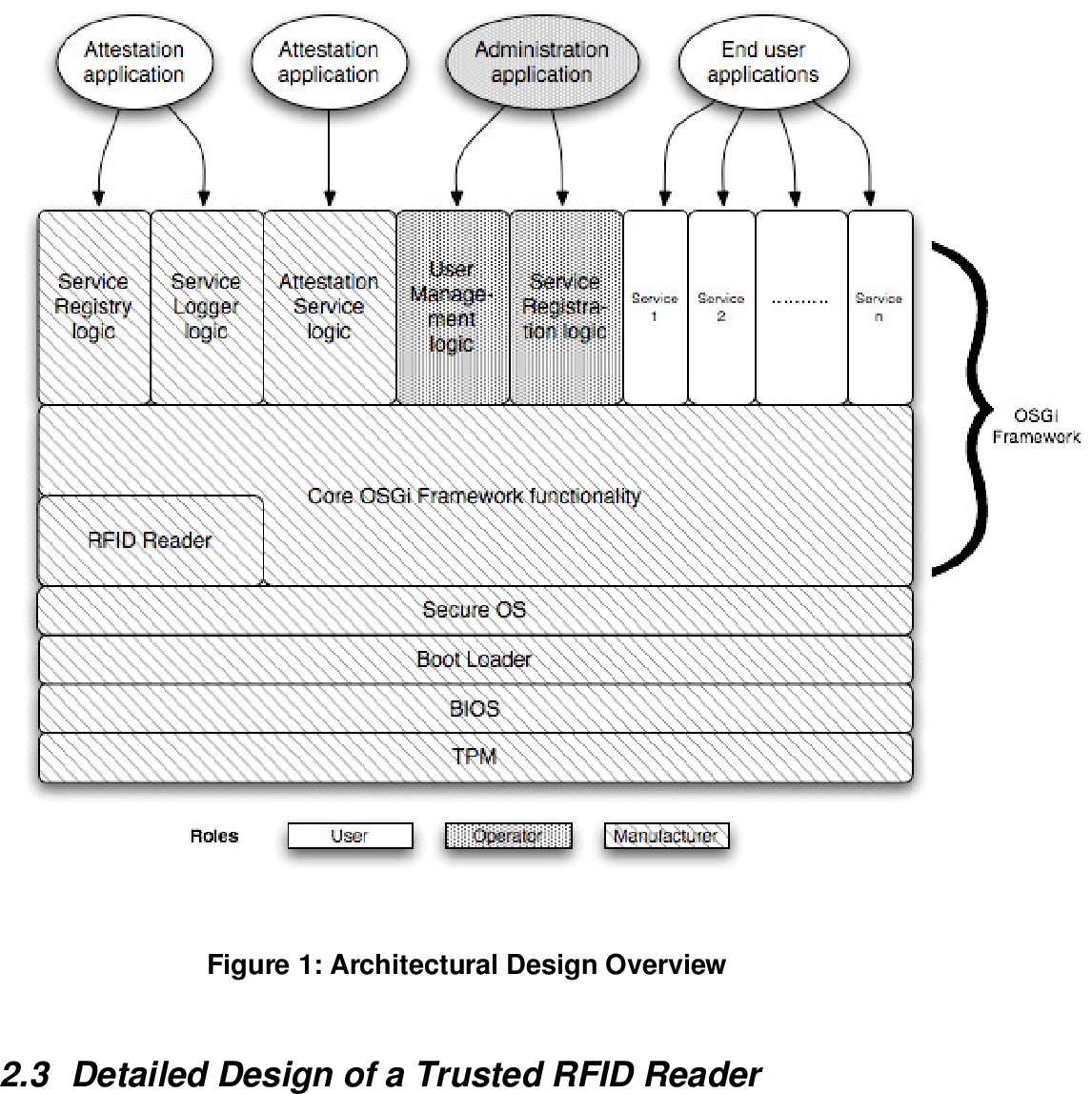 www.semanticscholar.org
www.semanticscholar.org
(PDF) CBDC-AquaSphere: Interoperable Central Bank Digital Currency
 www.researchgate.net
www.researchgate.net
Overview Of Ahoi Attacks | Ahoi Attacks
 ahoi-attacks.github.io
ahoi-attacks.github.io
Confidential Computing With Intel® Software Guard Extensions (Intel
 medium.com
medium.com
Hugo Profile
 shamiek.github.io
shamiek.github.io
(PDF) Enhancing The Privacy Of Network Services Through Trusted Computing
 www.researchgate.net
www.researchgate.net
Trusted Computing Base - Trusted Computing Base People Frequently Refer
 www.studocu.com
www.studocu.com
Trust Chain Of Trusted Computing Platform | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net
Dos Vulnerabilidades De Seguridad Encontradas En Trusted Platform
 noticiasseguridad.com
noticiasseguridad.com
Guilherme Araujo Thomaz
 www.gta.ufrj.br
www.gta.ufrj.br
(PDF) A Privacy Protection Framework For Medical Image Security Without
 www.researchgate.net
www.researchgate.net
Trusted Platform Module Library Part 3: Commands TCG Published - DocsLib
 docslib.org
docslib.org
Christopher Mansour, Ph.D., Associate CISO
 askmansour-internal.squarespace.com
askmansour-internal.squarespace.com
Trusted Computing Group Launches IoT Developer Resource Site - AB Open
 abopen.com
abopen.com
trusted computing group developer iot launches resource site
Trusted Computing And The Trusted Platform Module - A Hardware/software
 www.studocu.com
www.studocu.com
NUS CURIOSITY
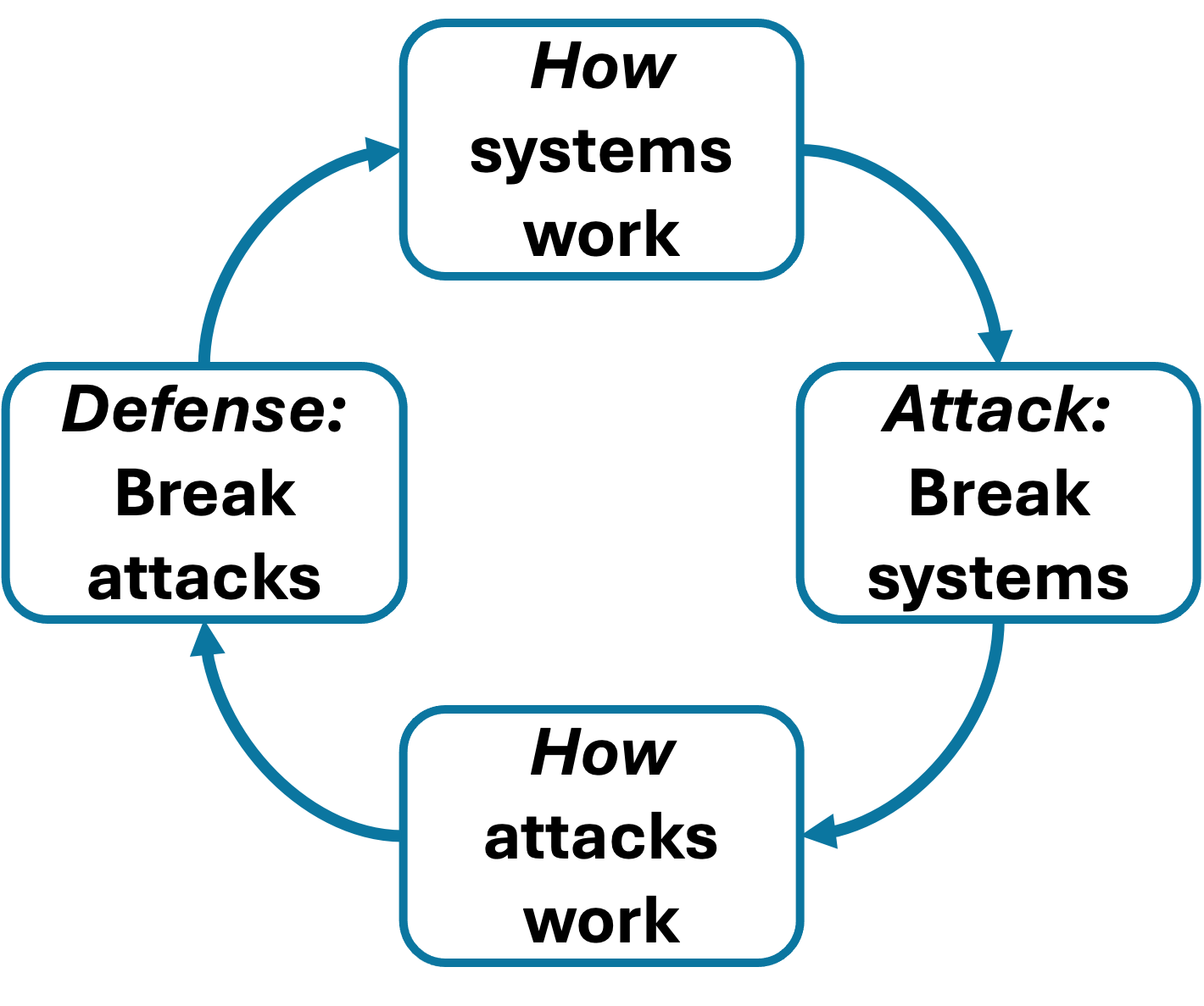 nus-curiosity.github.io
nus-curiosity.github.io
What Is A TCB: Understanding Trusted Computing Base - [Updated
 digitalgadgetwave.com
digitalgadgetwave.com
Trusted Computing - How Does A Streaming Site Protect Its Contents?
 blog.simonfarshid.com
blog.simonfarshid.com
(PDF) Solutions Guide For Data-At-Rest - Trusted Computing Group · SSIF
 dokumen.tips
dokumen.tips
What Is Hypervisor In Cloud Computing
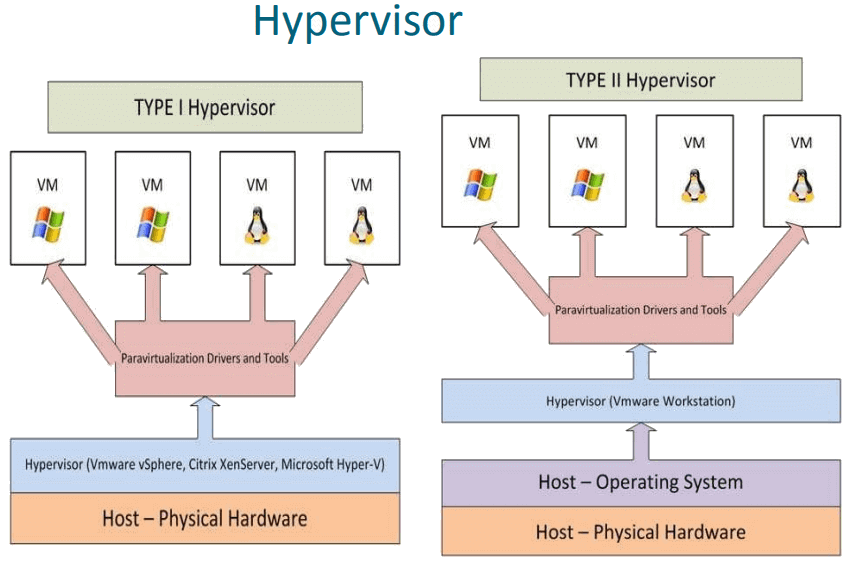 www.guru99.com
www.guru99.com
SOLUTION: IT244 Phoenix Wk 2 Developing Policies Related To Trusted
 www.studypool.com
www.studypool.com
SATA Cables | CDSG
 cdsg.com
cdsg.com
About | CDSG
 cdsg.com
cdsg.com
Confidential computing with intel® software guard extensions (intel. Dos vulnerabilidades de seguridad encontradas en trusted platform. 2025 4th international conference on cybersecurity, artificial